


The Cloud Atlas advanced persistent threat (APT) group has updated its weapons portfolio with polymorphic components that produce unique code for each infection.
Cloud Atlas, also known as inception, was first discovered by researchers in 2014 following attacks in Russia and Kazakhstan. At the time, the APT utilized CVE-2012-0158, an old vulnerability in Microsoft Office that can be exploited to perform remote code execution (RCE) attacks.
The threat actors remain active to the present day and have, once again, been linked to attacks in Russia, as well as Portugal, Romania, Turkey, Ukraine, and other countries.
On Monday, Kaspersky researchers said the spate of recent attacks is focused on “international economics and aerospace industries.”
In a blog post, the cybersecurity firm said the group is employing “a novel way of infecting its victims and conducts lateral movement through network.”
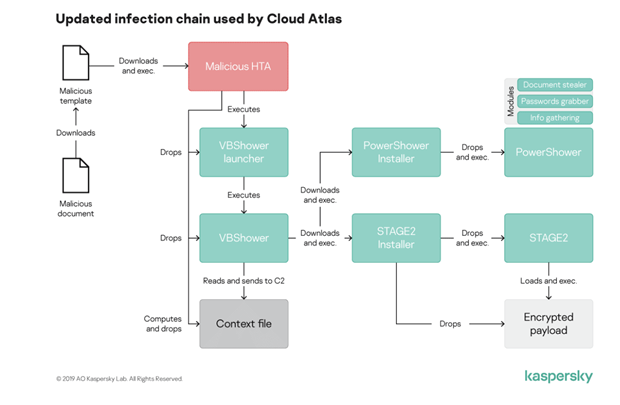
The first step in the infection chain is for hackers to send a phishing email to a high-value target. Each message includes a Microsoft Office document attachment which contains remote templates that, upon download, will deliver and execute malicious payloads.
A malicious HTML app will collect basic operating system information and download another module called VBShower. VBShower will remove as much evidence of infection from the target machine as possible and will also set up a communication channel between the malware and the operator’s command-and-control (C2) server.
Both the HTML and VBShower components are polymorphic, which means that their characteristics continually change in order to avoid detection by signature-based antivirus and security solutions.
“This updated version is carried out in order to make the malware invisible to security solutions relying on familiar Indicators of Compromise (IoCs),” Kaspersky says. “This means that the code in both modules will be new and unique in each case of infection.”
VBShower will also download another malicious module via VBS implant called PowerShower, which is a document stealer able to harvest .txt, .pdf, .xls or .doc files. Any document smaller than 5MB in size and that has been modified within 48 hours prior to infection will be stolen and sent to the C2.
This PowerShell-based module is also able to receive further PowerShell and VBS modules for execution on a victim’s machine, and contains a spying component which grabs lists of active processes — but this code does not appear to be fully active at this stage.
The APT group also uses a password grabber by way of the abuse of an open-source credentials recovery tool called LaZagne. Another backdoor used by Cloud Atlas may also be downloaded and executed, which was discovered five years ago and has not changed.

